Impact Analysis
Overview
The Impact Analysis feature provides powerful insights into your access control environment, helping you assess the potential consequences of changes before they are implemented. This proactive approach minimizes security risks and ensures operational continuity.
Impact Analysis comprises three distinct yet interconnected analysis types:
What-If Analysis
Least Privilege Analysis
Elevated Privilege Analysis
This document provides a detailed overview of each analysis type and its functionalities.
The Impact Analysis can be accessed through Entities → Applications → Application Details → Impact Analysis Tab.
What-If Analysis: Predicting the Ripple Effect of Changes
The What-If Analysis empowers you to simulate the removal or deletion of an entity (identity, resource, connection, or permission) and visualize its cascading impact on other entities within your environment.
How it works
Select Entity Type and Entity: From the dropdown menus, choose the desired entity type (identity, connection, resource, or permission) and then select the specific entity you want to analyze.
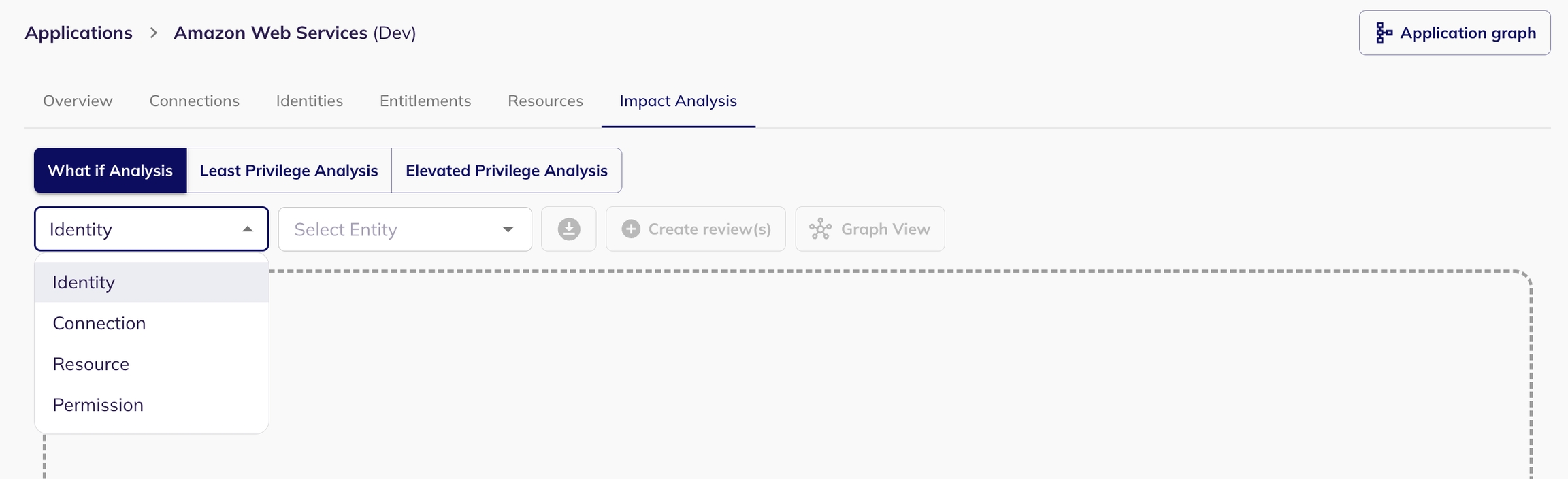
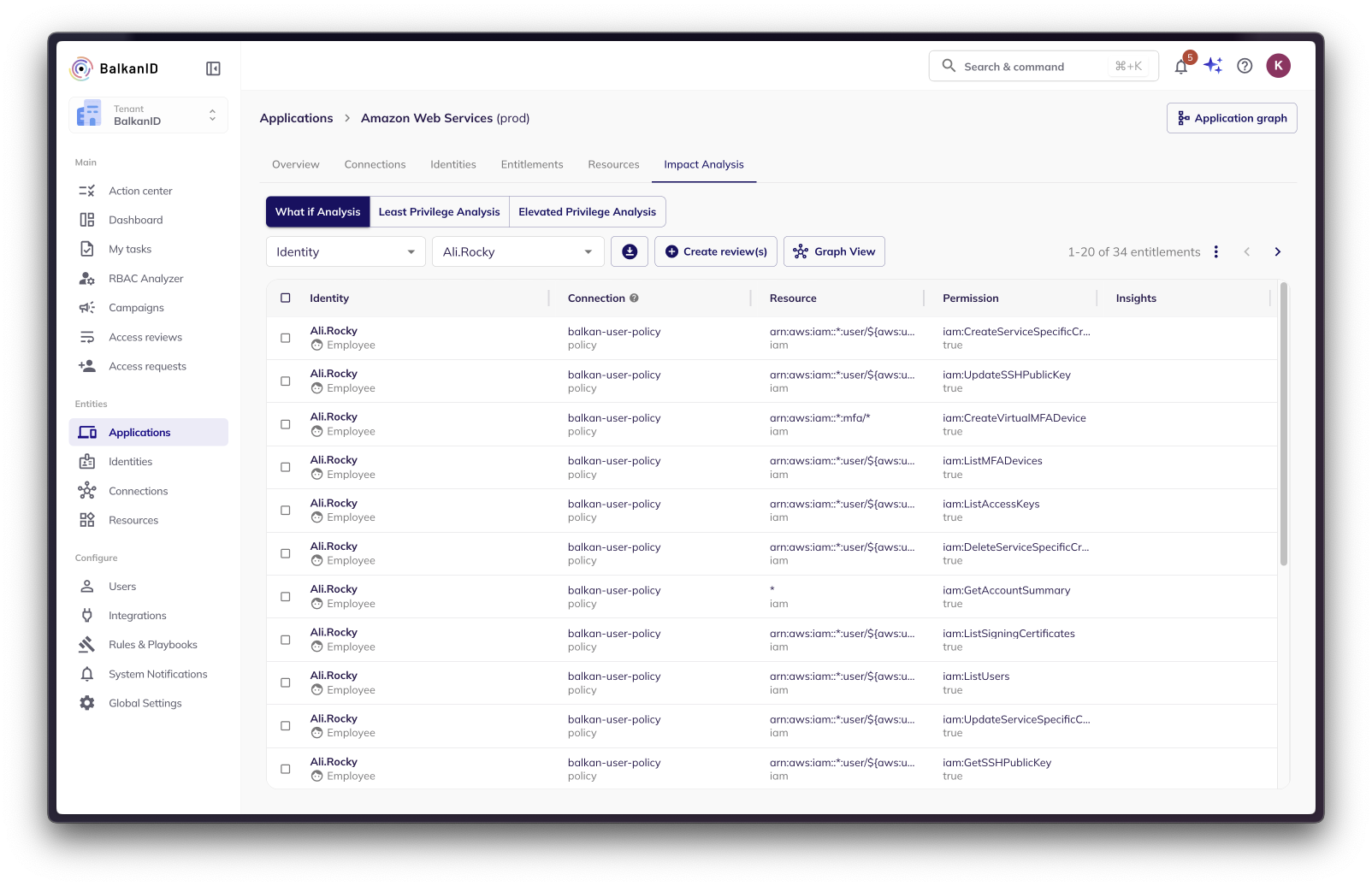
View Impact: The analysis results are presented in two intuitive views:
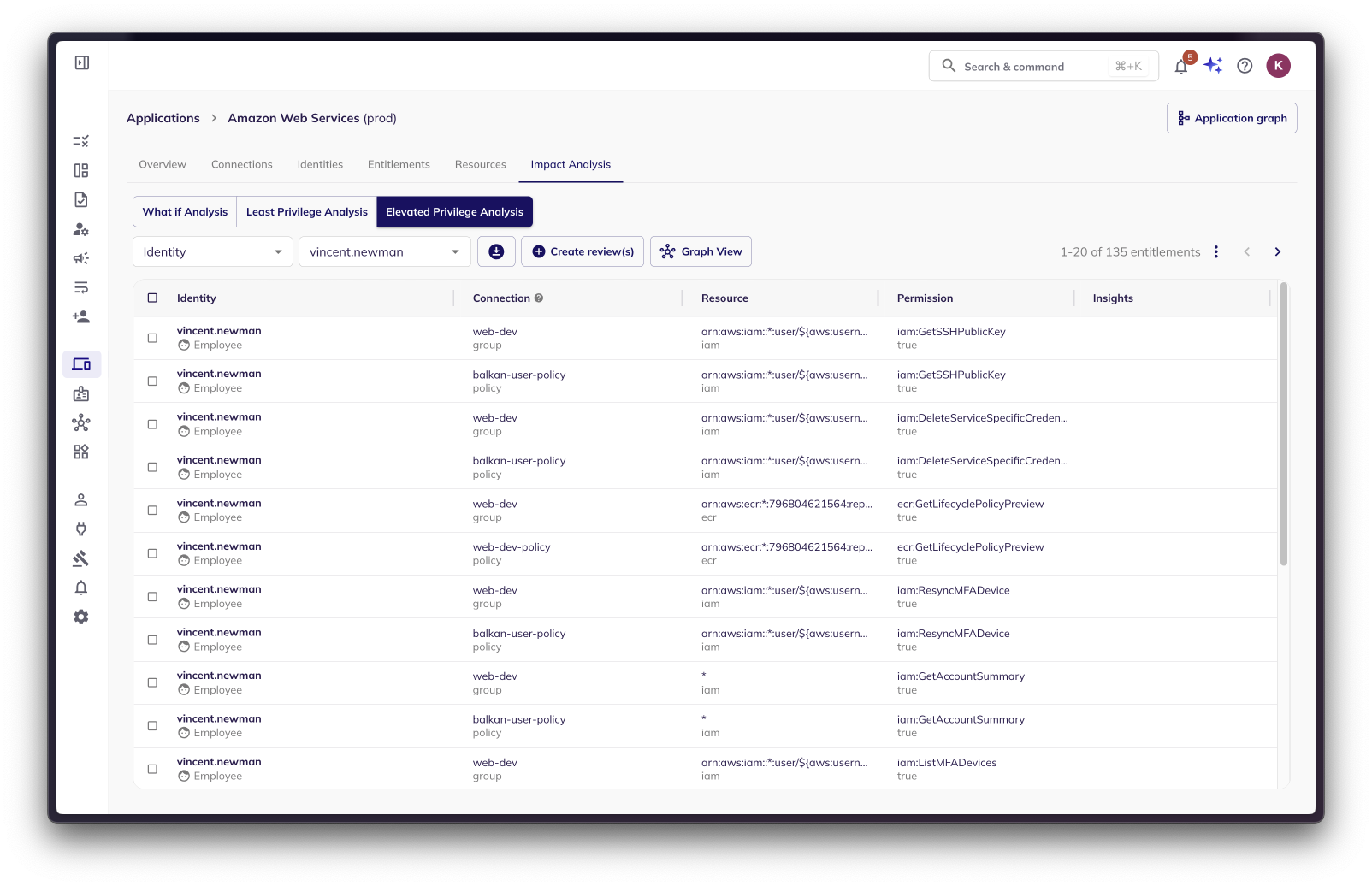
Tabular View: This view lists all the entitlements (permissions, access rights) that would be directly or indirectly impacted if the selected entity were removed. This list provides a comprehensive overview of potential access disruptions.
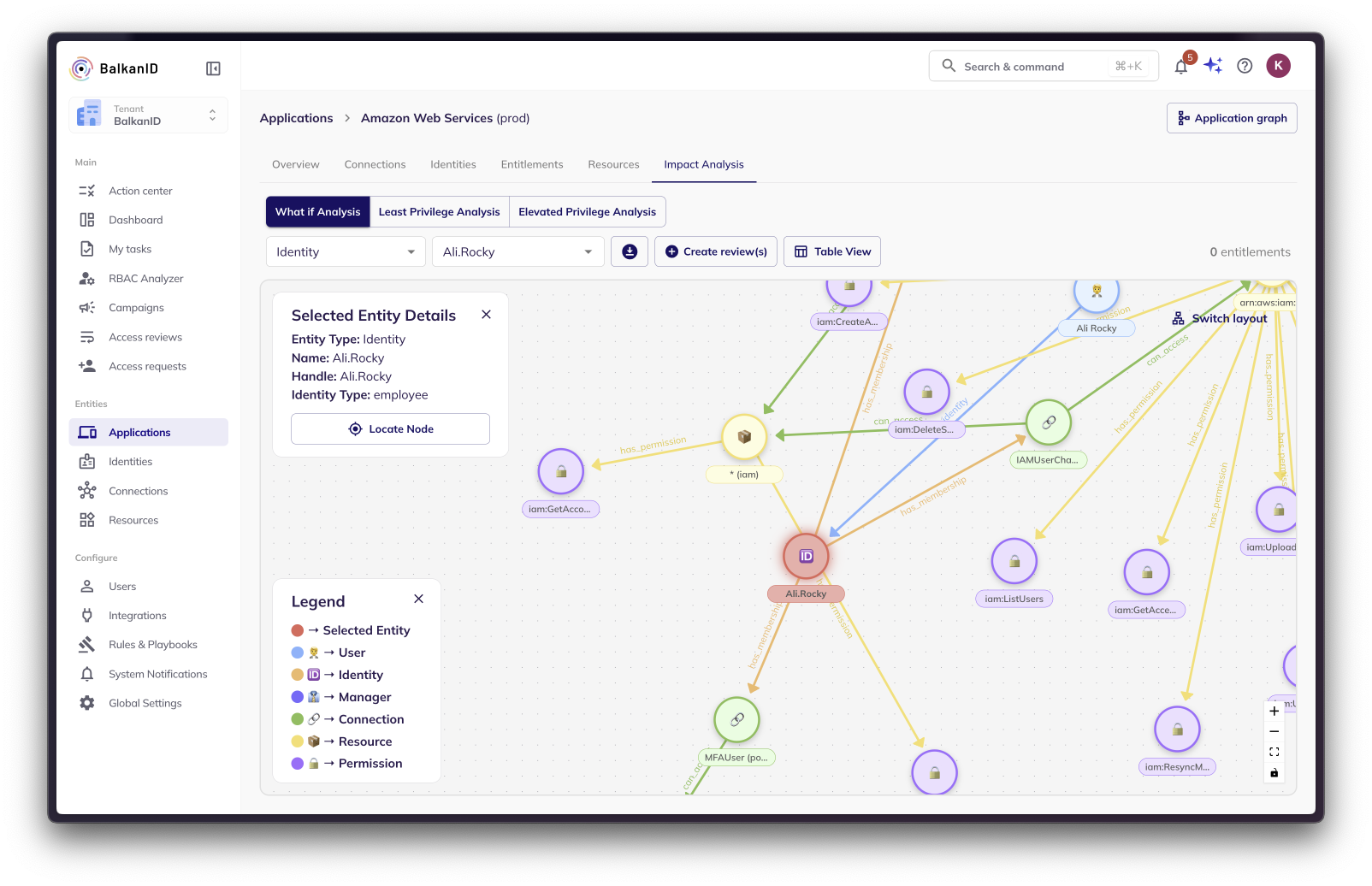
Graph View: This interactive visualization offers a clear and concise representation of the impacted entities and their relationships.
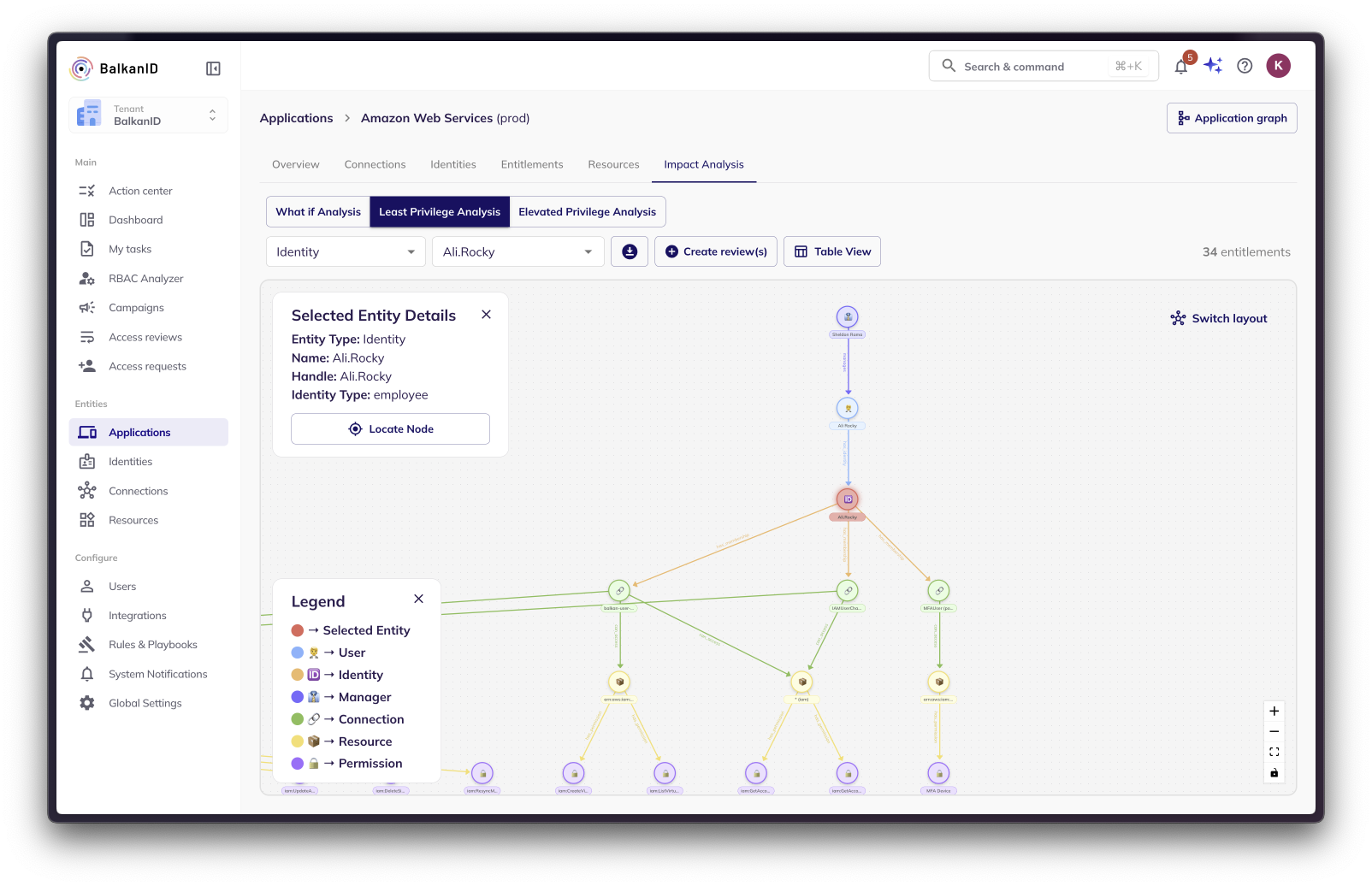
Selected Entity Highlighted: The entity selected for analysis is highlighted in red, making it easy to identify.
Color-Coded Entities: Other entities on the graph are color-coded according to their type (e.g., identities, connections, resources), as indicated in the legend.
Entity Details Panel: The selected entity's detailed information is displayed on the top-left of the graph.
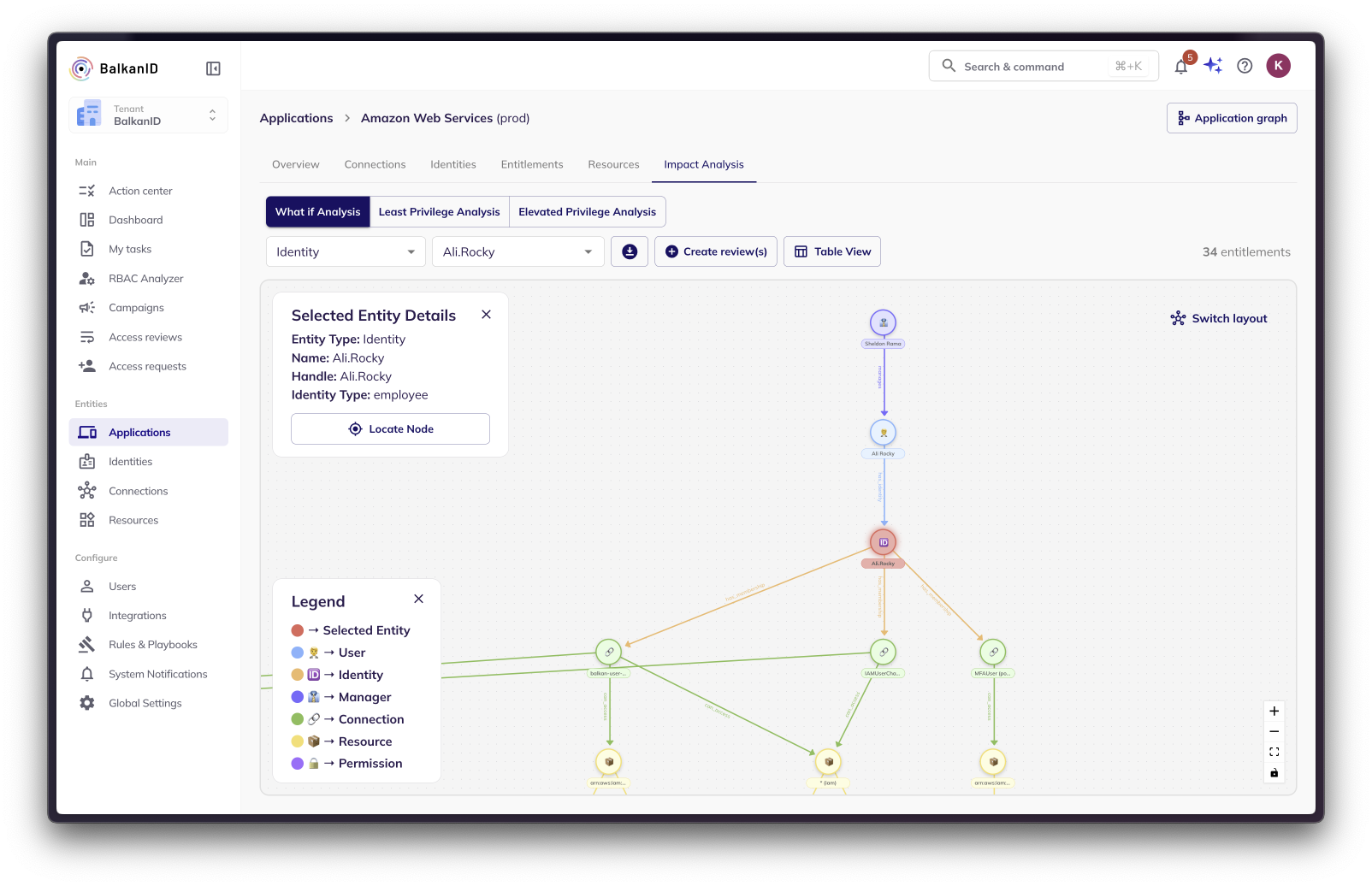
Layout Flexibility: You can switch between two graph layout options:
Force Layout: Offers a dynamic layout that automatically adjusts for optimal viewing.
Hierarchical Layout: Presents a structured, tree-like view of the relationships between entities.
Benefits
Proactive Risk Mitigation: Identify potential access disruptions and security risks before making changes.
Informed Decision Making: Make informed decisions about access control modifications based on a clear understanding of their impact.
Improved Security Posture: By understanding the ripple effects of changes, you can minimize the risk of unintended access or privilege escalation.
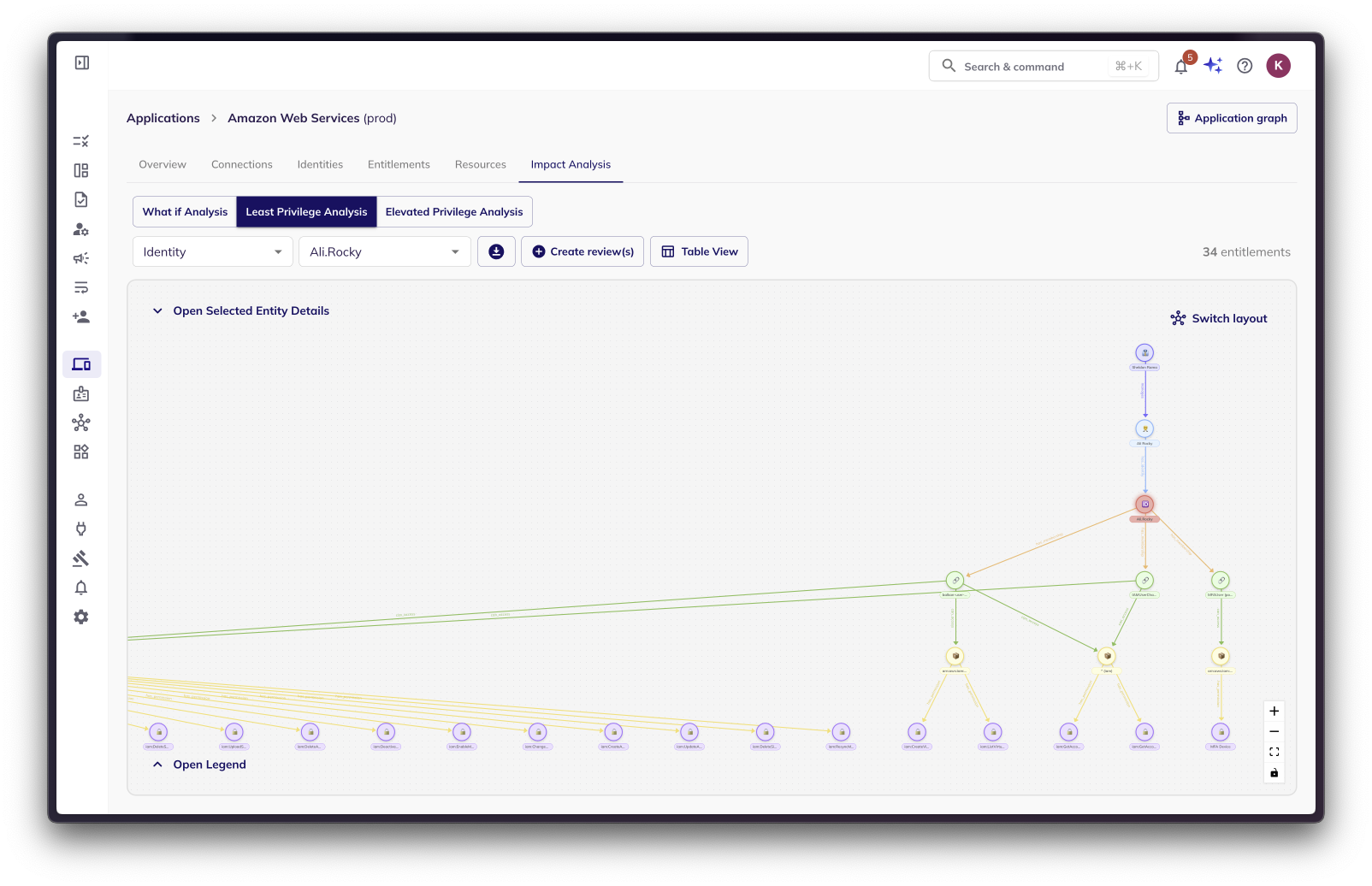
Least Privilege Analysis: Enforcing the Principle of Least Privilege
The Least Privilege Analysis helps you adhere to the crucial security principle of least privilege – granting entities only the minimum permissions necessary to perform their tasks.
How it works
The analysis leverages the RBAC Analyzer to examine the existing access control policies and user activity within your environment. It then determines the absolute minimum set of privileges required for each entity to effectively perform its intended functions.
Benefits
Enhanced Security Posture: By minimizing unnecessary privileges, you significantly reduce the attack surface and mitigate the potential damage from compromised accounts.
Improved Compliance: Comply with regulatory mandates and industry best practices that emphasize the principle of least privilege.
Optimized Access Control: Create a leaner, more efficient, and easier-to-manage access control environment.
Elevated Privilege Analysis: Spotting and Reviewing Questionable Access
Elevated Privilege Analysis focuses on identifying and reviewing access rights that deviate from established norms and might pose security risks.
How it works:
This analysis leverages the RBAC Analyzer to scrutinize access control policies and identify privileges that are deemed "questionable" or potentially excessive. These questionable privileges are flagged for further review.
The create review button can be used to automatically kick of an ad-hoc campaign to review the elevated entitlements.
Examples of Elevated Privileges
Overly Broad Access Compared to Peers: Entities granted access to a broader range of data than necessary for their roles.
Privileges Granted to Unmapped Accounts: Unmapped accounts retaining access privileges, posing potential security risks.
Unnecessary Administrative Rights: Users granted administrator-level privileges when their roles only require standard user permissions.
Benefits
Proactive Threat Detection: Identify potential privilege escalation paths.
Improved Access Governance: Strengthen your overall access control governance by addressing anomalies and maintaining a least privilege model.
Reduced Risk of Insider Threats: Minimize the risk of malicious insiders exploiting excessive privileges for unauthorized activities.
Accessing Impact Analysis Features:
All three analysis types are seamlessly integrated within the Impact Analysis page (Entities → Applications → Application Details → Impact Analysis). You can easily switch between them using the dedicated toggle buttons.
Both the tabular and graph views are available for all analysis types, providing consistent and comprehensive insights regardless of the analysis you perform.
For more detailed information or assistance, please contact BalkanID support ([email protected]).
Was this helpful?

