Identities Entitlements Discovery
Overview
In this article we will explain how to use the Identities page for entitlement discovery. Here you will see a list of all the identities in your BalkanID environment, which includes employees, service accounts, and unmapped identities. You can use the filter menu or search bar to drill down for individual identities or groupings of identities, such as identity types, departments, or managers.
Keep in mind that this a list of application identities, not employees or service accounts, and multiple identities are often tied back to one employee or service account.
To navigate to the Identities page follow the below steps:
Click on Entities from the lefthand navigation sidebar to open the drop down.
Select the Identities page from the drop down.
You can view the various identities associated with different applications.
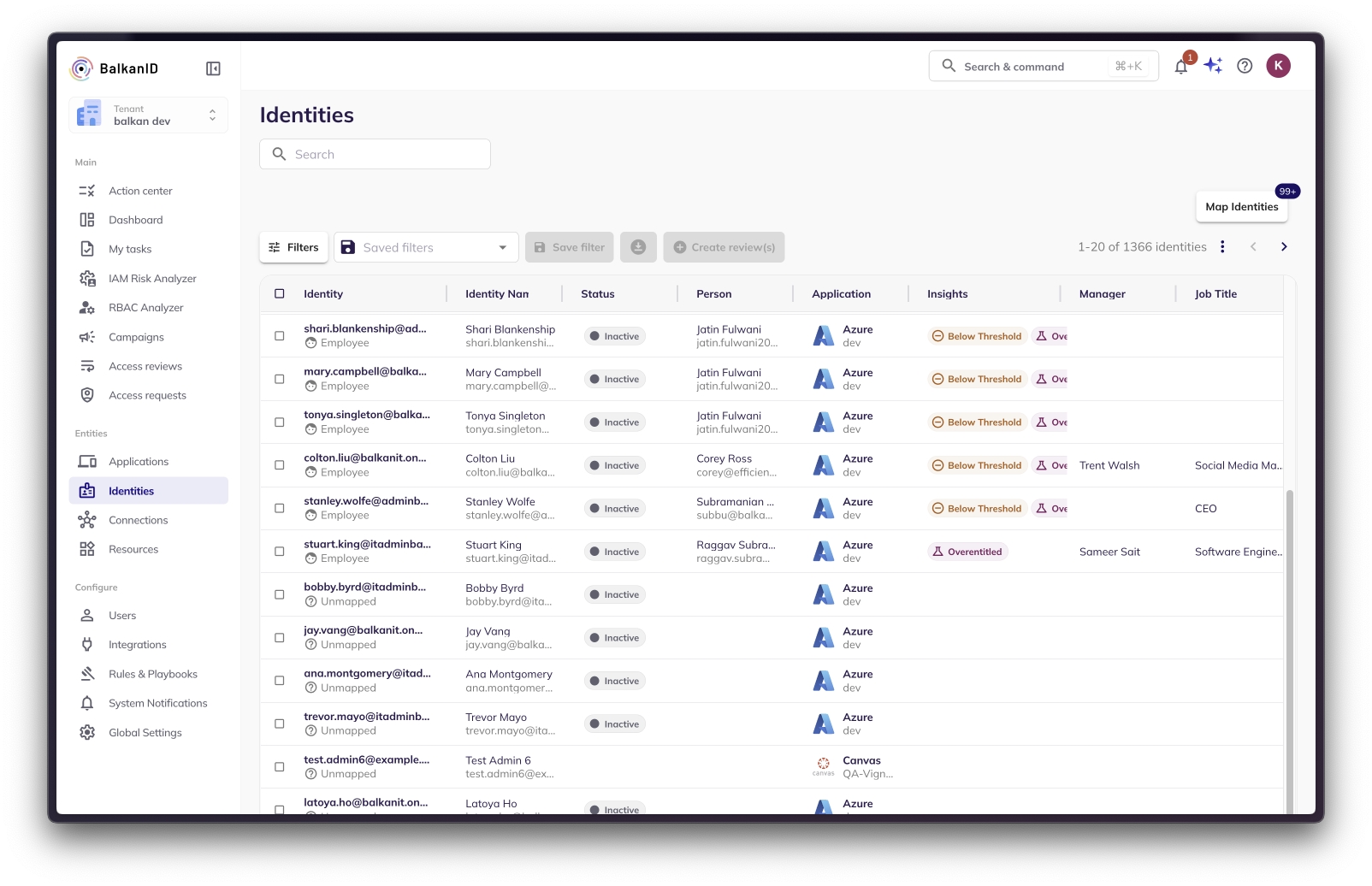
You can use the search box and filters to explore the applications integrated. The following filter fields are available for this page:
Identity - This field filters data based on the specific identity within an application. For example, to view information about r-droid101 in the GitHub(test) integration, use "r-droid101 (github test)" as a filter in this field.
Identity type - You can filter your identities based on a user being an employee, service account or an unmapped identity.
Status - You can filter your identities based on whether the identity is active or inactive.
Identity Name - This field filters data based on the name of the identity irrespective of the application integration type. For example, to view information about raggav identity in all AWS integrations, enter the filter in this field.
Person - You can use this filter to look for identities that belong to a particular employee. For example, to see all the identities that belong to an employee Alice, select "Alice" as a filter in this field.
Application - This field filters based on the specific Application Integration that you would like to explore. For example, to view identities within Azure(Test Environment) data, add it as a filter in this field.
Connection - This field allows you to filter data based on a connection in an application. For example, to view all identities associated with the admin connection in a group connection type within Confluence, add it as a filter in this field.
Connection Type - This field filters data based on the type of connections available. For example, to view all the identities that belong to a group connection type, add it as a filter in this field.
Resource - This field is used to filter out identities which have privileges to a resource. For example, to view all the identities that have access to the sales vault in 1password, pass "1password/vault/sales" as a filter in this field.
Resource Type - This field is used to filter out identities which have privileges to a resource type. For example, to view all the identities that have access to different vaults in 1password, pass "1password/vault" as a filter in this field.
Insights - Filtering with insights allows you to see which identities have insights on them. For example, to view the identities which are Privileged, you can add "Privileged" as a filter in this field.
Manager - You can filter identities based on the manager of the employee that this identity is tied to. For example, to find all the identities associated with employees managed by Sameer Sait, add him as a filter in this field.
Job Title - You can filter identities based on the job title of the employee that this identity is tied to. For example, to find all the identities associated with employees with the job title as ML Engineers, add it as a filter in this field.
Department - You can filter identities based on the department that the employee belongs to. For example, to find all the identities associated with employees in the Engineering department, add it as a filter in this field.
Employment Type - You can filter identities based on the employment type of the employee that this identity is tied to. For example, to find all the identities associated with "part-time intern" employees, add it as a filter in this field.
Permission - The Permission field allows you to filter identities based on the permission they have to a resource. For example, to view all identities which have read permission on repositories in GitHub, add "github/read" as a filter in this field.
Permission Value - The Permission value field allows you to filter identities based on the permission value they have to a resource. For example, to view all identities which have true permission value, add it as a filter in this field.
Using multiple filter fields together will help you navigate through the data swiftly and will make your time spent on discovering entitlements a lot more productive! Refer to working with filters to learn more about filters.
Viewing Individual Identity page:
Clicking on an identity will bring up more information about their entitlements. You can use a similar filter menu to sort by the permissions, groups, or resources that this identity has access to.
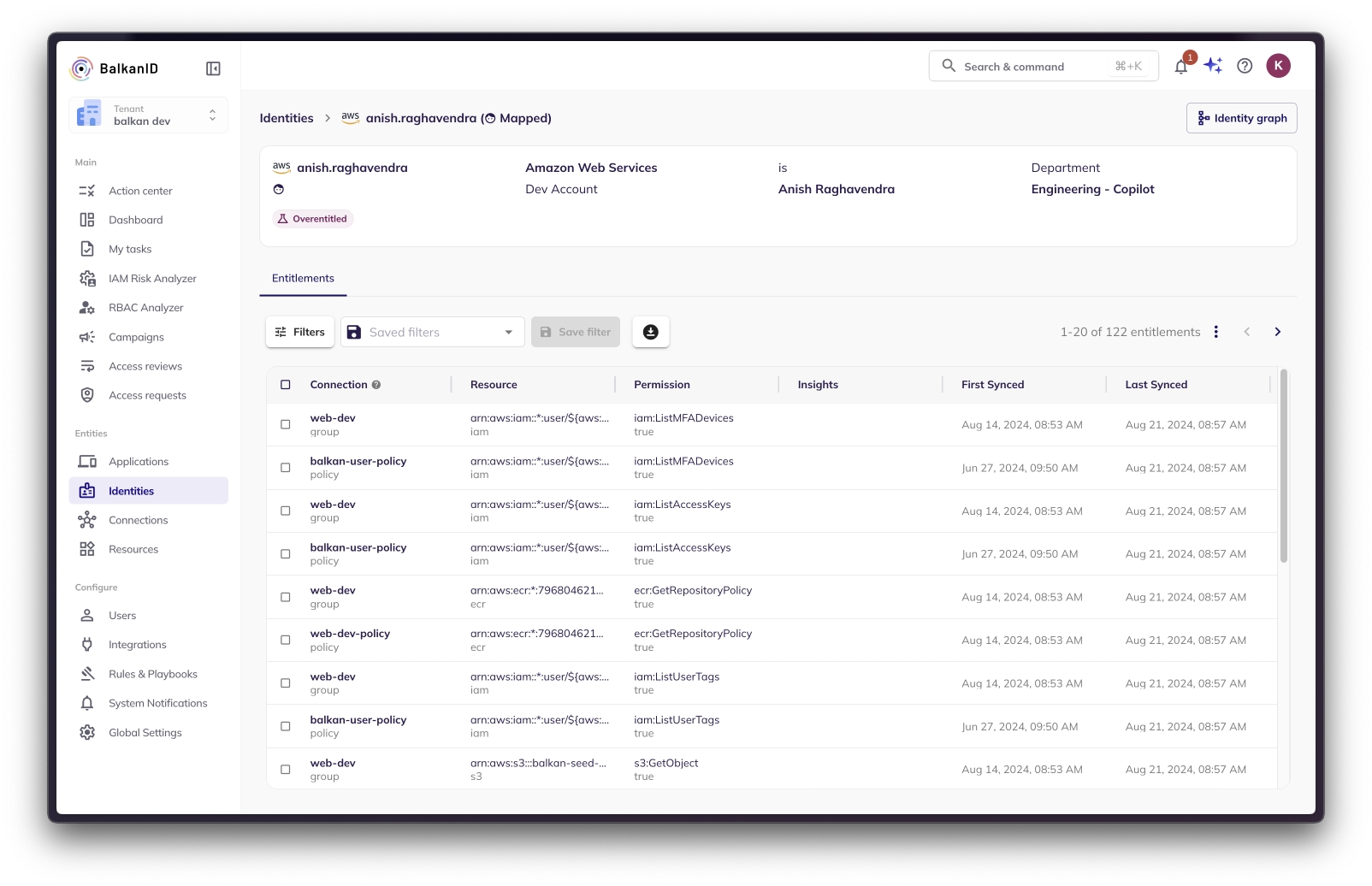
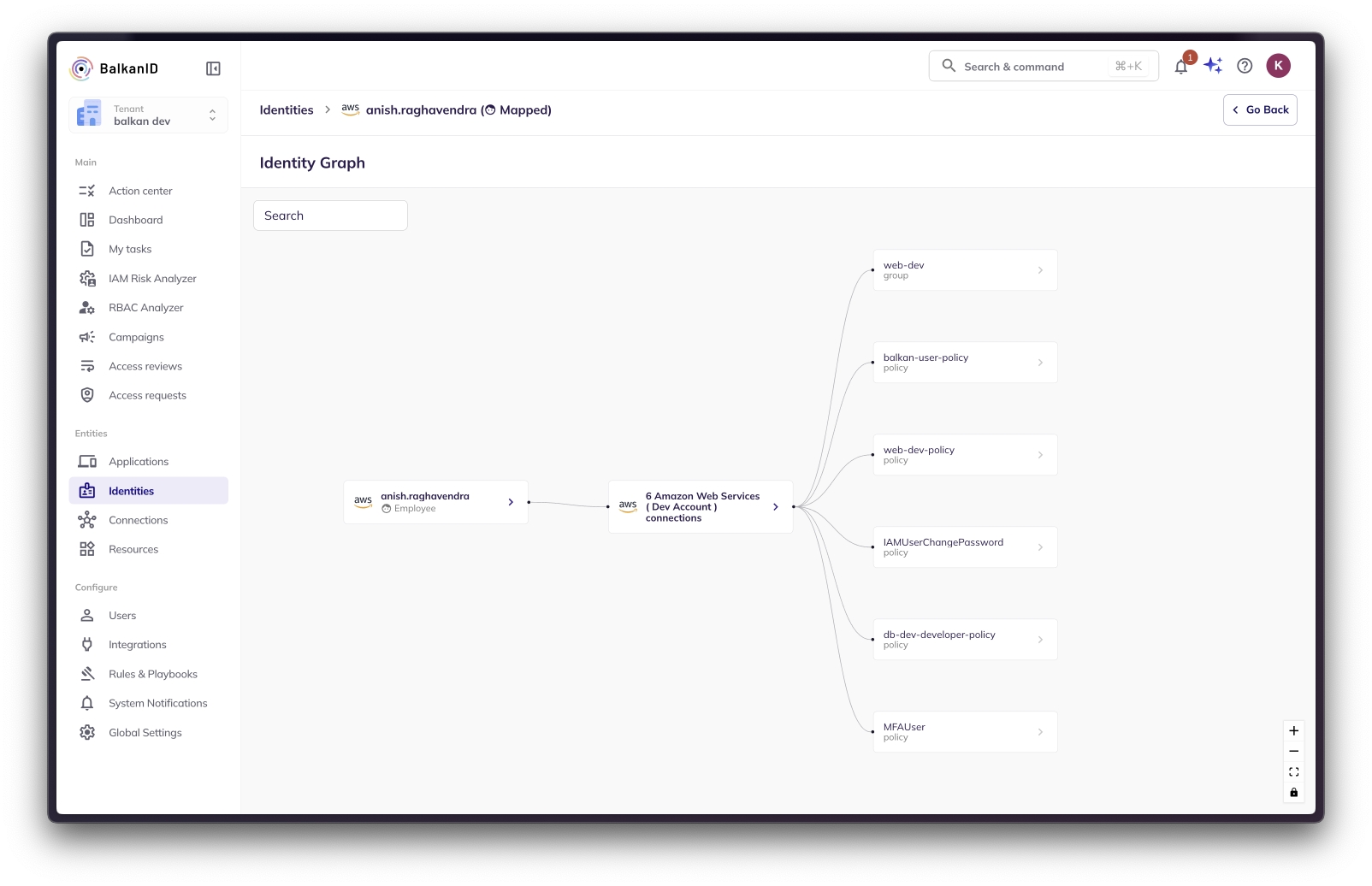
Identities Graph View
The Identities Graph View on the top right corner of the image above, will allow the user to visualize the identity-entity relationships in a manner that helps understand lineage and dependancies. In the example screenshots below, you are able to see how identity -> application -> resources/permissions are related.
Was this helpful?

